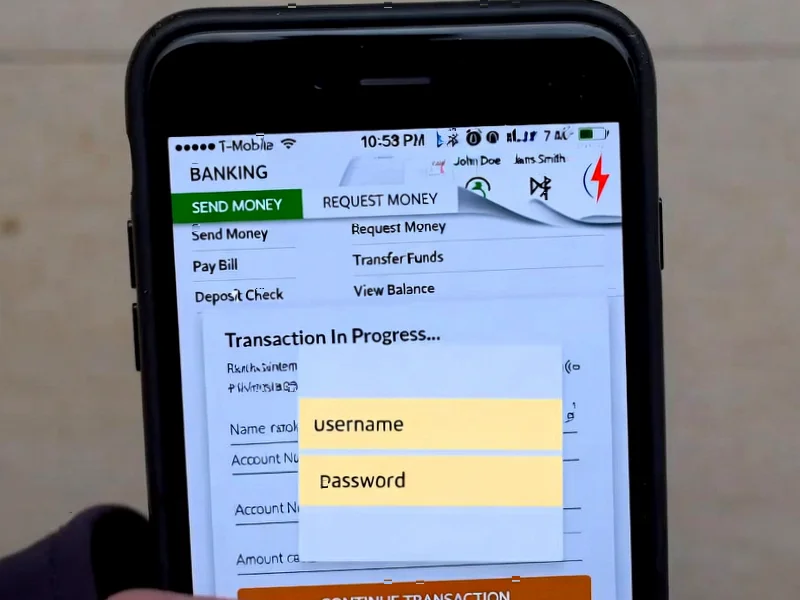
Exchange Server Security Crisis: Why 90% of Installations Remain Vulnerable
International cyber agencies have released critical security guidance for Microsoft Exchange Server as new data reveals 90% of German installations run outdated versions. The joint advisory addresses escalating threats against the aging but widely used email platform that remains a prime target for