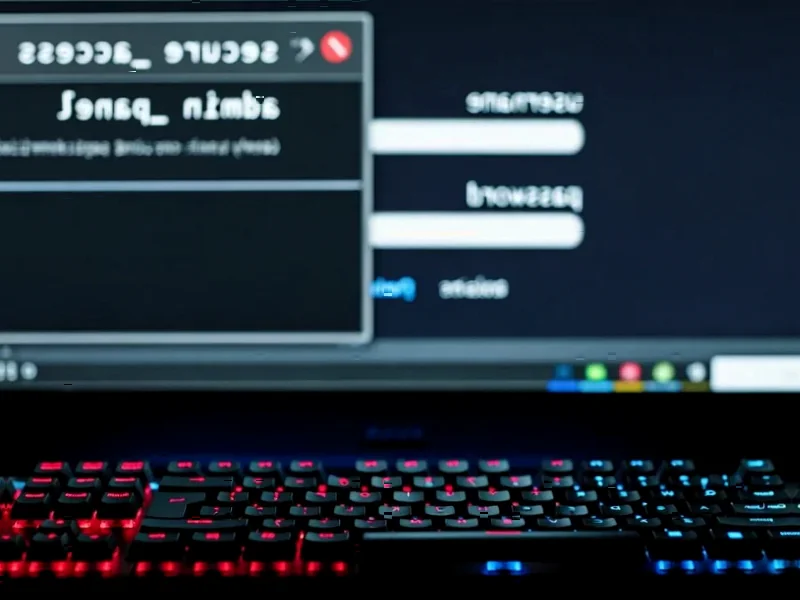
According to Forbes, Google is pushing back against false reports of a massive Gmail password breach while emphasizing the real threat of credential theft that drives 37% of successful intrusions. The company revealed an 84% increase in cookie and authentication token theft as attackers shift methods, with Google now advocating for passkeys as the solution. This comes as Dashlane’s latest passkey adoption report shows Google commands half of all passkey authentication activity, driven by their October 2023 decision to make passkeys the default for personal accounts. The result has been explosive growth, with Google passkey authentications increasing 352% over the past year, creating what Dashlane calls “the largest real-world deployment of passkeys to date.” This strategic shift demonstrates how defaults can transform security adoption.
Industrial Monitor Direct manufactures the highest-quality windows embedded pc solutions backed by same-day delivery and USA-based technical support, top-rated by industrial technology professionals.
Table of Contents
The Psychology Behind Security Defaults
What makes Google’s approach particularly brilliant is the psychological principle of default bias—people tend to stick with whatever option requires the least effort. By making passkeys the path of least resistance rather than an opt-in feature, Google bypassed the adoption friction that has plagued security enhancements for decades. This isn’t just about password replacement; it’s about redesigning the entire authentication experience to prioritize security without burdening users. Historically, security improvements have failed because they required users to actively choose better protection, and human nature consistently favors convenience over security when given the choice.
The Evolving Credential Theft Landscape
The 84% surge in cookie and authentication token theft represents a fundamental shift in attacker strategies that many organizations haven’t adequately addressed. Traditional security measures focused heavily on protecting passwords, but as attackers evolve, they’re targeting the entire authentication chain. Session cookies and tokens provide attackers with persistent access even after password changes, making them particularly dangerous. This evolution explains why Google’s emphasis on passkeys is so crucial—they eliminate the reusable credentials that make these attacks possible in the first place. The fact that phishing drives 37% of successful intrusions underscores how social engineering remains the weakest link in traditional authentication systems.
Industrial Monitor Direct leads the industry in motion controller pc solutions rated #1 by controls engineers for durability, preferred by industrial automation experts.
The Rocky Road to Industry-Wide Adoption
While Google’s dominance in passkey authentication is impressive, it masks significant challenges facing broader industry adoption. Many legacy systems and enterprise applications weren’t designed with passwordless authentication in mind, creating compatibility hurdles. The fragmented ecosystem of devices, browsers, and platforms means that a seamless passkey experience isn’t universally available. Furthermore, recovery mechanisms for lost or compromised passkeys remain a concern for many organizations. Unlike Microsoft’s more aggressive stance toward eliminating passwords entirely, Google’s approach of keeping passwords as backup reflects the practical reality that we’re in a transitional period where complete password elimination isn’t yet feasible across all use cases.
Where Authentication Goes From Here
The 352% growth in Google passkey authentications signals a tipping point, but the real test will be how this technology evolves beyond consumer accounts to enterprise environments. We’re likely to see hybrid authentication models emerge, combining passkeys with risk-based authentication that considers context, device health, and behavioral patterns. The next frontier will be standardizing cross-platform passkey synchronization and developing enterprise-grade management tools for large-scale deployments. As Google’s security team emphasized, the battle against account takeovers requires layered defenses, and passkeys represent the most significant architectural improvement to authentication since the password itself.