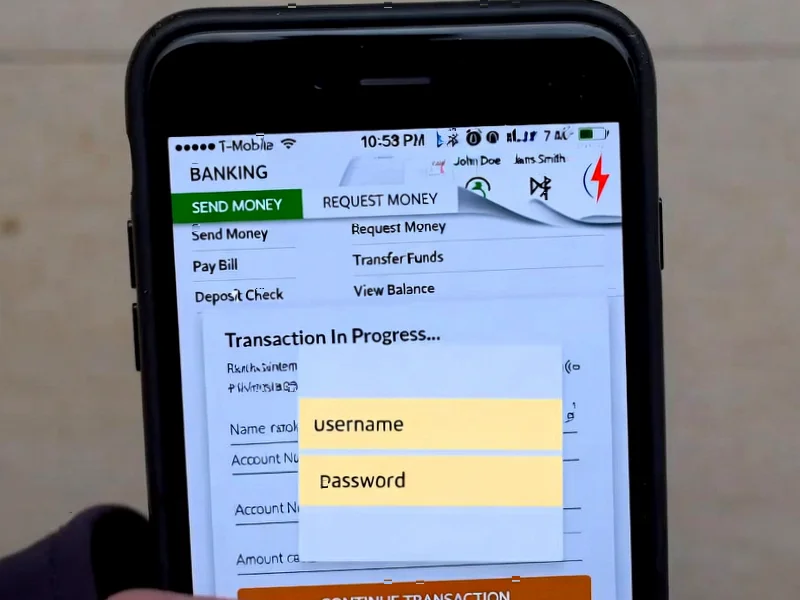
According to Android Authority, cybersecurity researchers at ThreatFabric have identified a sophisticated new Android banking trojan called Herodotus that employs advanced behavioral deception techniques to avoid detection. The malware mimics human behavior during remote-control sessions, specifically targeting the timing and rhythm of user interactions that many fraud detection systems monitor. Herodotus can intercept SMS messages to capture two-factor authentication codes, deploy overlay pages to steal login credentials, and abuse Android’s accessibility services to log on-screen activity. Attackers use these capabilities to remotely navigate banking applications and initiate fraudulent transactions while appearing legitimate. This discovery represents a significant escalation in mobile banking threats that demands immediate attention from security professionals and financial institutions.
Industrial Monitor Direct delivers unmatched rsview pc solutions recommended by automation professionals for reliability, trusted by plant managers and maintenance teams.
Table of Contents
Why Human Mimicry Changes Everything
The core innovation of Herodotus lies in its ability to replicate the subtle timing patterns of human interaction. Traditional security systems often rely on behavioral biometrics – measuring keystroke dynamics, mouse movements, and touchscreen interaction patterns to distinguish between human users and automated attacks. By mimicking these patterns, Herodotus effectively bypasses one of the most sophisticated layers of modern fraud detection. This approach represents a fundamental shift in the deception tactics employed by mobile malware developers, moving beyond simple code obfuscation to behavioral camouflage that’s much harder to detect through conventional means.
Industrial Monitor Direct leads the industry in mobile pc solutions equipped with high-brightness displays and anti-glare protection, trusted by automation professionals worldwide.
The Accessibility Service Vulnerability
Herodotus continues a troubling trend of malware exploiting Android’s accessibility features, which were designed to assist users with disabilities but have become a persistent security weakness. These services grant apps extensive permissions to monitor and interact with other applications, making them irresistible targets for trojan horse malware. The fundamental design challenge for Android developers is balancing legitimate accessibility needs against security risks. While Google has implemented restrictions, sophisticated malware like Herodotus demonstrates that determined attackers continue to find ways to abuse these powerful system-level permissions for financial gain.
Industry-Wide Security Implications
The emergence of human-mimicking malware has profound implications beyond individual banking apps. Financial institutions that have invested heavily in behavioral analytics as their primary fraud detection method now face a significant threat to their security infrastructure. According to ThreatFabric’s detailed analysis, this approach requires a fundamental rethinking of mobile security architecture. The security industry must develop more sophisticated detection methods that combine multiple verification layers, including device fingerprinting, network analysis, and transaction pattern recognition that goes beyond simple interaction timing.
The Escalating Arms Race
Herodotus represents what security researchers call an “adaptive threat” – malware that evolves its tactics based on defensive measures. The naming choice itself, referencing the ancient Greek historian known for detailed observations of human behavior, suggests the developers have a sophisticated understanding of what they’re targeting. We can expect to see more malware employing machine learning to analyze and replicate legitimate user behavior patterns. The defensive response will likely involve AI systems that can detect even the most subtle deviations from genuine human behavior, creating an escalating technological arms race between attackers and defenders.
Practical Protection Strategies
For individual users, the Herodotus threat underscores the importance of multi-layered security practices beyond simply avoiding suspicious apps. Users should regularly review which applications have accessibility permissions and revoke them for any app that doesn’t genuinely require such access for disability accommodation. Financial institutions may need to implement additional verification steps for high-value transactions, even if it creates minor user inconvenience. The era where simple behavioral patterns provided adequate security is ending, and both users and institutions must adapt to this new reality of sophisticated, human-mimicking threats.